With EventLog Analyzer's improved log processing rate, security administrators can easily handle the exponential growth in the flow of log data as they expand.
EventLog Analyzer version 10 can process the log data at high processing speed of 20,000 logs per second with the peak event handling capacity up to 25,000 logs per second.
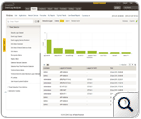 EventLog Analyzer enhances its reporting console by adding 1000+ out-of-the-box reports across Windows, Unix/Linux, network devices, and application infrastructure which help in meeting your security, operational and compliance needs.
EventLog Analyzer enhances its reporting console by adding 1000+ out-of-the-box reports across Windows, Unix/Linux, network devices, and application infrastructure which help in meeting your security, operational and compliance needs.
These reports are meticulously drafted and categorized so as to reduce the time for creating custom reports for regular activities thus increasing the operational efficiency of security administrators. Read More »
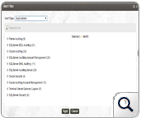 With the enhanced real-time event response system, comes 500+ predefined alert criteria.
With the enhanced real-time event response system, comes 500+ predefined alert criteria.
Security administrators can now set up alert criteria for the occurrence of critical security events, operational events, attacks and more across Windows, Unix/Linux, network devices and application infrastructure, without creating a custom alert profile. Read More »
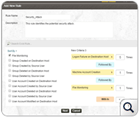 EventLog Analyzer's correlation engine extends to accommodate the correlation rule builder that allows security administrators to define known attack patterns that help in proactively mitigate security threats.
EventLog Analyzer's correlation engine extends to accommodate the correlation rule builder that allows security administrators to define known attack patterns that help in proactively mitigate security threats.
With the flexible drag n drop interface, correlation rule builder allows security admins to combine different predefined rules to form an attack pattern. Security administrators can also specify threshold limits for individual rules thus reducing the false positives.Get real-time alert notification via email or SMS upon the occurrence of the attack pattern thus preventing the data breach even before it happens. Read More »