This Document describes the steps involved in Setting up Desktop Central in a Demilitarized Zone. It also explains how Desktop Central can be used effectively in various network scenarios.
DMZ works by creating a network security zone in which services can be accessed from trusted and untrusted networks alike. One or more firewall can be used to create the DMZ ensuring that sensitive and critical data resides safely on the DMZ. Generally computers which are located within DMZ are designed to receive most of the incoming traffic (requests that are received into DMZ from outside network) but strictly restricts the outgoing traffic(requests that are sent out from DMZ to Outside network).
Using Desktop Central to manage computers in a DMZ makes desktop management simpler and easier without compromising the security aspects of the network. Since there are different ways to to design a network with a DMZ, installing Desktop Central requires few prerequisites, which are based on the customers network design. We would require to open few ports in the firewall which are customer specific and harmless to network.
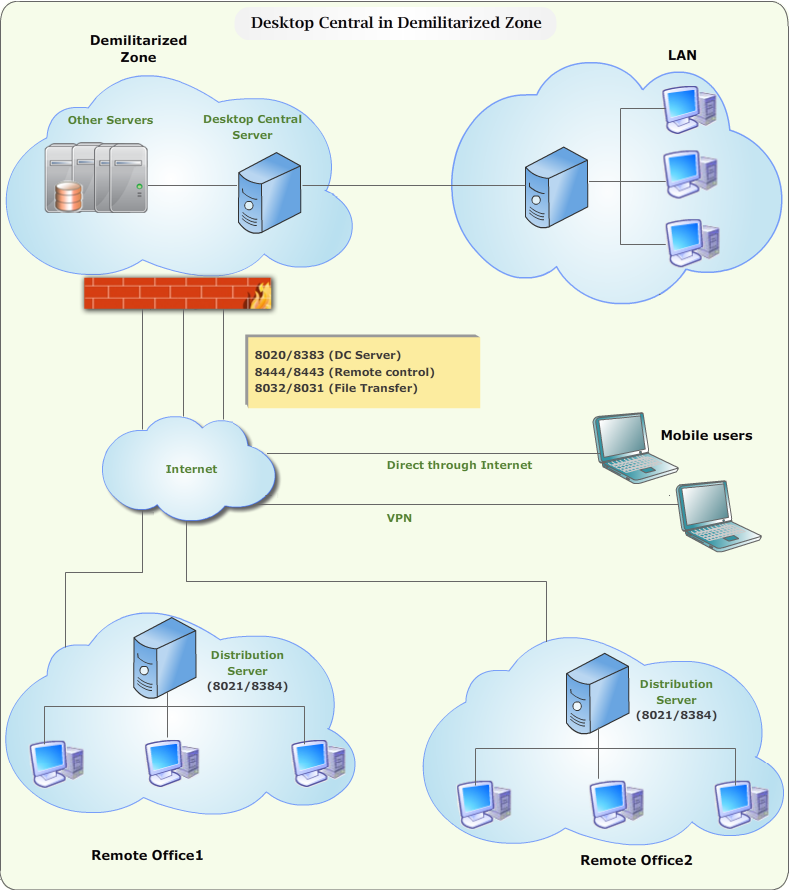
Ports to be Opened in DMZ:
When Desktop Central Server is installed in the DMZ, the following ports should be opened in the firewall to allow the Desktop Central Agents to communicate with the Desktop Central Server.
Note: All the ports are inbound to the Desktop Central Server. The data flow would be both the ways - inbound and outbound.
8020: Used for agent-server communication and to access the Web console
8383: Used for secured communication between the agent and the Desktop Central server
8443: Used to control computers remotely (secure mode)
8444: Used to control computers remotely
8031: Used to transfer files (secure mode)
8032: Used to transfer files
8027: Used to perform on demand operations.
5223: port should be open, if the mobile device connects to the internet through the WiFi, it is recommended to configure the IP range 17.0.0.0/8.
5228, 5229 & 5230 Inbound port - Used by the GCM to reach the managed mobile devices
In this scenario Desktop Central server is installed inside the DMZ zone. Desktop Central Agents are installed in the computers which are located in the LAN, and the remote locations. Once the Desktop Central agents are installed, managing computers using Desktop Central from DMZ becomes very easy. As per the default DMZ rules, all incoming traffic will be permitted to reach the Desktop Central Server. Desktop Central agents from LAN, remote offices, and mobile users will communicate with the Desktop Central Server periodically. So there would be no hinderance for the agents to reach the Desktop Central Server, and communication remains the same in though the Desktop Central Server is located in DMZ.
Tasks
Desktop Central Server which is located in the DMZ will be restricted to allow outgoing traffic. So Desktop Server will be restricted to reach the internet, this would result in hindering few services of the Desktop Central Server, which needs to be addressed. Since Desktop Central Server cannot permit the outgoing traffic, the following tasks of Desktop Central would be affected.
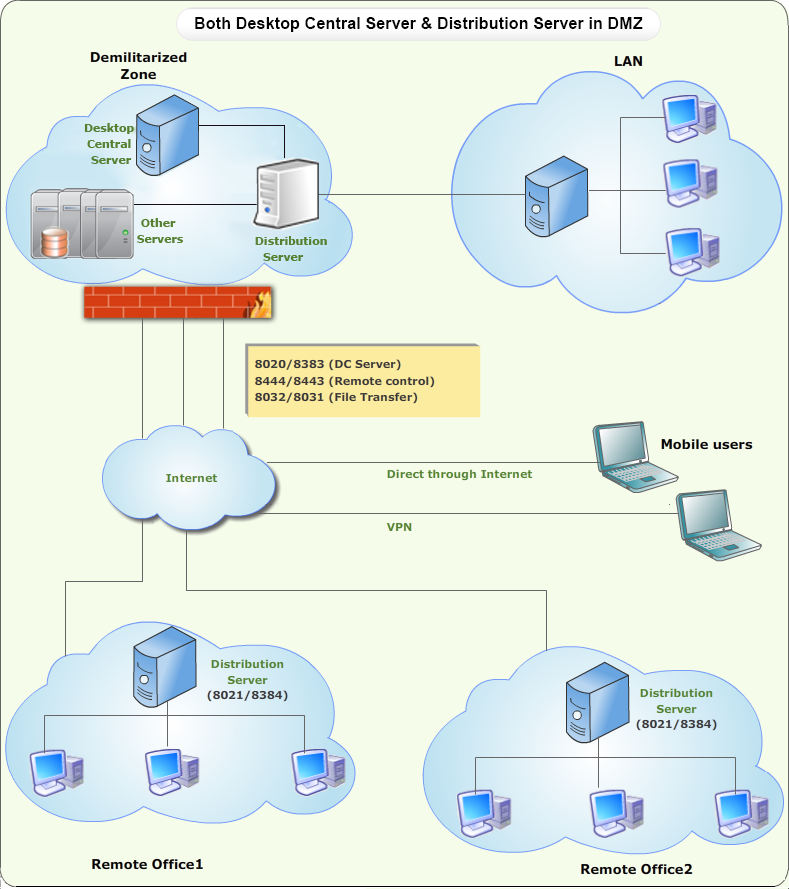
In some network scenarios, administrators prefer not to disclose the location of the Desktop Central Server due to security reasons. In such cases, the location of the Desktop Central Server is not disclosed to any of the computers that need to be managed in the LAN and remote location. Installing a Distribution Server in DMZ to manage all the computers in DMZ and a remote location can be done. So the Distribution Server is addressed as the central server for all the Desktop Central Agents.

So, all the computers in LAN, remote location and mobile users can be managed using Desktop Central installed in the DMZ. If you find any difficulties in setting up the network, kindly contact support for further assistance.